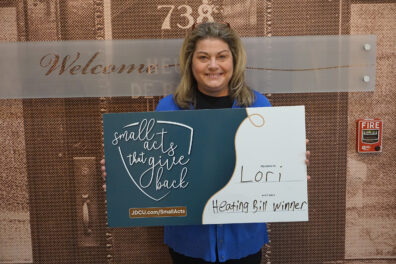
Jeanne D’Arc Heating Bill Winners
Jeanne D’Arc Credit Union held its annual Small Acts That Give Back Heating Bill campaign, which is an initiative aimed … Continue reading

The Money Mill
Jeanne D’Arc Credit Union will never call and ask you for your security or account information. If you receive a call claiming to be from us and looking for this information, please hang up and call us at 978-452-5001.
Jeanne D’Arc Credit Union will never call and ask you for your security or account information. If you receive a call claiming to be from us and looking for this information, please hang up and call us at 978-452-5001.
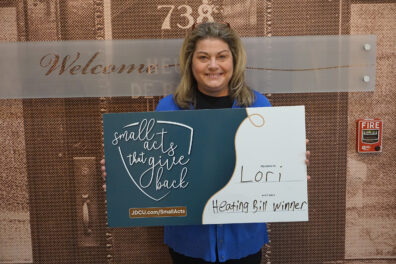
Jeanne D’Arc Credit Union held its annual Small Acts That Give Back Heating Bill campaign, which is an initiative aimed … Continue reading

Lowell, MA (April 18, 2024) – Mark S. Cochran, President and Chief Executive Officer of Jeanne D’Arc Credit Union, recently … Continue reading

Practical money management skills learned at an early age can have a lasting impact on the rest of your child’s … Continue reading

As adults, how we handle finances sends a powerful message to children. That’s why it’s important to model the healthy … Continue reading

We hope you have enjoyed our series highlighting strong, female voices throughout Jeanne D’Arc Credit Union. Thank you to all … Continue reading

In the past weeks, we have celebrated International Women’s Day and Women’s History Month by highlighting several female voices who … Continue reading

Whether you’re looking to get your first credit card for everyday expenses or take out a mortgage to purchase your … Continue reading

Even though International Women’s Day has passed, we believe that celebrating the incredible women on the Jeanne D’Arc team should … Continue reading

The prevalence of self-care messaging reminds us to nurture our physical and mental well-being—with mindfulness practices, exercise routines, and virtual … Continue reading

With so many incredible women contributing to the Jeanne D’Arc team, we’re keeping the International Women’s Day celebration rolling! Throughout the … Continue reading